Our Blog
Our Blog
This server is running on a Node.js pod on a Kubernetes cluster. An nginx ingress controller forces all HTTP connection to redirect to HTTPS. SSL is rated A+ by Qualys SSL Labs having implemented HTTP Strict Transport Security (HSTS) and DNS Certification Authority Authorization (CAA) Policy. SSL Certficates are provided by Let's Encrypt and renewals are automated using cert-manager.
Nagios Plugins for Kubernetes
We are sharing with the community the Nagios Plugins we have written for Kubernetes which focuses on Prometheus. This is also our first project hosted on Gitlab since we decided to move out of Github in the light of Microsoft's acquisistion of the latter. Microsoft has since embraced Open Source but Gitlab support of free Private repositories are essential for sensitive projects to still be hosted.
Please click on the title to take you to the Gitlab repository.
Service Reliability Hierarchy
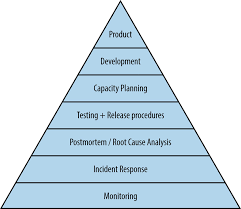
Monitoring is the foundation of Service Reliability. Without it you will be working blind. Only at the time when users complain that you will know there is a problem. The objective of monitoring is to know a problem will occur before the users find out. This way you will have time for decision-making on how to attack the impending incident.
What is Your Industry?
An owner of one of the largest bank in the country have said that his company is a technology company with financial-domain expertise. The board laughed at him in secret. Today, his bank is leading in embracing technology and proves that his vision is a requirement for companies to survive. Indeed, to be a competitive company today one must fully adopt technology and maximize it to the fullest to gain advantage over your competitor.
Minimum Features When Building a Mail Server
Our mail server has a corresponding Reverse DNS. Bind is replicated via AXFR to BuddyNS. Plain SMTP does not allow relaying and has a rate limiter using fail2ban. Authentication via SMTP Submission for Postfix and IMAPS using Dovecot.
It is equipped with additional security features like SPF, DMARC, DKIM and RBL. It is protected against Directory Harvest Attack (DHA).
It is also not enough that you are running SSL. Not all protocols and ciphers are equal. We only enabled the Strongest ones.
Use this command to check your ciphers and their strength. nmap --script=ssl-enum-ciphers <target>
There is also a new way to limit issuing authority to issue certificates for your domain. So if you are using Let's Encrypt, you need to add these lines to your DNS server:
This domain's DNS certificates are protected by CAA.
yourdomain.com. IN CAA 128 issue "letsencrypt.org"
yourdomain.com. IN CAA 128 issuewild ";"
yourdomain.com. IN CAA 128 iodef "mailto:user@yourdomain.com"
sub.yourdomain.com. IN CAA 128 issue "letsencrypt.org"
Here 128 means maximum enforcement
issuewild ";" means don't authorize anyone to issue wildcards and
iodef means send any issues or violations to this email. You also need to do that for every subdomain you need.
Cloud-Native Meets DevSecOps
This server is running on a Node.js pod on a Kubernetes cluster. An nginx ingress controller forces all HTTP connection to redirect to HTTPS. SSL is rated A+ by Qualys SSL Labs having implemented HTTP Strict Transport Security (HSTS) and DNS Certification Authority Authorization (CAA) Policy. SSL Certficates are provided by Let's Encrypt and renewals are automated using cert-manager.
 Joebert Jacaba
Joebert Jacaba